Editor's Note: Read part one of this series.

On May 15th 2018, we published this post announcing that some of our customers fell victim to a deserialization-based remote control execution (RCE) vulnerability. In the majority of cases, a subset of the gadget chain (circumstances to exploit the deserialization vulnerability) were triggered by customer application’s dependency on one or more 3rd party Software-as-a-Service SDKs, which in turn depends on a vulnerable version of jackson-databind, an OSS JSON data-binding library. This vulnerability is particularly tricky to catch, because it is contextual: The exposure comes from how various libraries interact with each other.
Listed below is an excerpt from the NVD feed pertaining to this vulnerability
{
"id": "b85a00e3-7d9b-49cf-9b19-b73f8ee60275",
"title": "[CVE-2017-17485] Improper Control of Generation of Code (\"Code Injection\")",
"description": "FasterXML jackson-databind through 2.8.10 and 2.9.x through 2.9.3 allows unauthenticated remote code execution because of an incomplete fix for the CVE-2017-7525 deserialization flaw. This is exploitable by sending maliciously crafted JSON input to the readValue method of the ObjectMapper, bypassing a blacklist that is ineffective if the Spring libraries are available in the classpath.",
"cvssScore": 9.8,
"cvssVector": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"cve": "CVE-2017-17485",
"reference": "https://ossindex.sonatype.org/vuln/b85a00e3-7d9b-49cf-9b19-b73f8ee60275"
},
{
"id": "4f7e98ad-2212-45d3-ac21-089b3b082e6c",
"title": "[CVE-2018-7489] Incomplete Blacklist, Deserialization of Untrusted Data",
"description": "FasterXML jackson-databind before 2.7.9.3, 2.8.x before 2.8.11.1 and 2.9.x before 2.9.5 allows unauthenticated remote code execution because of an incomplete fix for the CVE-2017-7525 deserialization flaw. This is exploitable by sending maliciously crafted JSON input to the readValue method of the ObjectMapper, bypassing a blacklist that is ineffective if the c3p0 libraries are available in the classpath.",
"cvssScore": 9.8,
"cvssVector": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"cve": "CVE-2018-7489",
"reference": "https://ossindex.sonatype.org/vuln/4f7e98ad-2212-45d3-ac21-089b3b082e6c"
}
In the prior post we expressed the desire of extracting intelligence from the textual description illustrated above and representing it as an actionable semantic template.
If we were to do this, how would it be represented ?
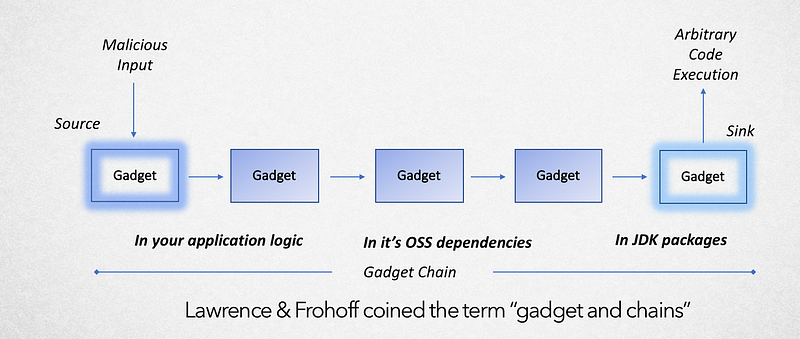
Tatu Saloranta (aka Cowntowncoder) did a fabulous job describing conditions associated with this vulnerability.
- Use version of Jackson that does not (yet) block “gadget” class in question
- Has at least one specific “gadget” class that works with Jackson-Databind to exploit in the Java classpath
- Enable polymorphic type handling for properties with nominal type of
java.lang.Object(Default typing is enabled viaObjectMapper) - Accepts JSON content sent by untrusted client (sending maliciously crafted JSON input to the readValue method of the ObjectMapper)
Let us analyze this application using Ocular and investigate the contextual conditions leading to an exploit.
For the next set of steps, you will need to request for free trial on Ocular distribution here (with SCA package).
After installing Ocular distribution, execute the following commands. As a composite it will inspect for all conditions (semantic template) that will lead for this exploit to be successful.
Step 1: Get Dependencies
At this junction, we have the application’s CPG loaded in scope of active session.
Step 2: Get Active CVEs associated with the dependencies (direct and transitive)
Let us now query for active CVEs associated with the bill of materials. We will use Ocular SCA package (based on Sonatype’s OSSIndex REST controller) to identify active CVEs.
Amongst several active CVEs above (edited) let us draw attention to jackson-databind dependency that is vulnerable.
Step 3: Construct semantic template to query for conditions to trigger vulnerability
As next steps we will build out the semantic template to verify if all these conditions exists to trigger the gadget exploit.
With the combination of semantic template (conditional and flow signatures) associated with CVE records and Ocular, we can establish whether a OSS vulnerability is exploitable or not. Based on the outcome, one can prioritize which vulnerabilities need remediation.
Photo: Egor Kamelev



.png?width=610&name=J1_ModernCybersecurityBook_Promo%201200x628%20v2@2x%20(1).png)



