Why do the bad guys keep winning?

Hacker stereotype
Well, for starters, there are misconceptions about who the bad guys even are, says Kate Healy of Telstra. This guy, dressed in a hoodie, is how the public thinks of a malicious hacker. But that's inaccurate — they look like you, or me.
Perhaps at one time, this vandalizing loner represented the biggest security threat. Back when hackers were people who, well, hacked, for the fun and thrill of it. But this isn't how things are today.
Why do we still have breaches, then?
- Because of the way we think of security. It's not a gated state, but a process. "Am I secure?" is the wrong question.
- Modern environments are extremely complex, and complexity is the enemy of security. Applications that we use have tens of millions of lines of code, with just as many opportunities for mistakes and misconfigurations.
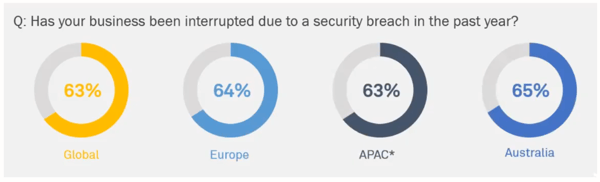 And we have a lot of breaches. As you can see above, no matter how/where you slice it, nearly 2/3rds of companies have been interrupted by breaches. The three most common forms of attack are web application attacks, business email compromises, and human error.
And we have a lot of breaches. As you can see above, no matter how/where you slice it, nearly 2/3rds of companies have been interrupted by breaches. The three most common forms of attack are web application attacks, business email compromises, and human error.
Years ago, when Kate would say that she worked in cybersecurity, people didn't really understand this very well. And, she and her team were "kept in the basement." They were usually brought in reluctantly and too late for prevention, and organizations viewed them as drag on software development.
These days, security has more of a first class role, and the rise of agile methodologies and DevOps have helped. But there are still challenges and a long way to go.
Consider that security is really a form of risk, which is a very business-facing concern. Mention risk in the C-suite, and you'll have everyone's attention. So it's interesting that security — risk management at its core — is delegated to inside of the IT organization. And this becomes even more fascinating and disturbing when you consider that two of the three most common most common attack vectors involve human error and social engineering.
Here's an interesting example.
A newly installed CFO receives an email apparently from the CEO, requesting a funds transfer, and complies. She sends a text to the CEO to confirm, and the CEO immediately calls and raises an alert, which surfaces that this was, in fact, a false email. When you think about this, an organization can solve for this just as easily, if not more so, with process than with technology.
And this demands a two-pronged approach to security, involving technology and people.

Because security is, in fact, an organization-wide concern, we're seeing a rise in the Chief Information Security Officer (CISO) role. This role does not report to the CIO, but rather directly to the CEO: a development which allows the security organization to be far more cross-cutting.
As a result, cybersecurity organizations are taking on more of a governance and advisory role, meaning that DevOps teams might find themselves more hands-on with security, engaging security folks in a more advisory capacity.
But that shift has led to confusion about what all the cybersecurity group actually owns. Things wind up falling to them by default.
We often confuse security with privacy, even though they are not the same thing.
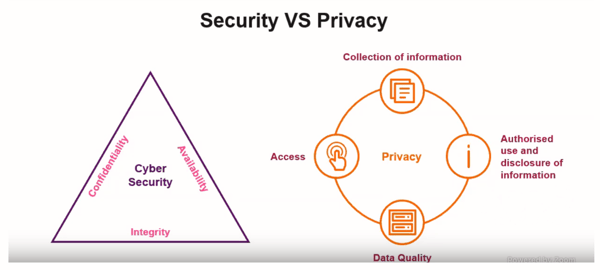 With security, we tend to talk about protecting the data and the system along three axes: confidentiality, integrity, and availability. With privacy, we're more interested in protecting data about an individual. How do we collect information, disclose, and access it? And what kind of quality of data do we have?
With security, we tend to talk about protecting the data and the system along three axes: confidentiality, integrity, and availability. With privacy, we're more interested in protecting data about an individual. How do we collect information, disclose, and access it? And what kind of quality of data do we have?
However, there are some commonalities regarding controls. This includes activities like installing firewalls, putting authentication in place, etc. This results in similar processes and institutions and the data and privacy concern falling on the cybersecurity team by default.
This is a common, but not the only, example of things falling to the cybersecurity organization. They might inherit responsibility for regulatory compliance and other concerns as well, when people don't know where else to go.
Risk is Not Bad
All of these concerns that may fall to the cybersecurity team revolve around the idea of risk: security, privacy, regulatory compliance, etc. And, while businesses clearly want to minimize and control risk, risk itself is not inherently bad.
In order to accomplish things and get ahead, businesses have to take risks. So risk management becomes not about eliminating risk, but minimizing the impact of what happens when things go wrong. And this is best done by aligning policies and activities with minimizing that impact.
This post was written by Erik Dietrich. Erik is a veteran of the software world and has occupied just about every position in it: developer, architect, manager, CIO, and, eventually, independent management and strategy consultant. This breadth of experience has allowed him to speak to all industry personas and to write several books and countless blog posts on dozens of sites.
Photo by Soumil Kumar



.png?width=610&name=J1_ModernCybersecurityBook_Promo%201200x628%20v2@2x%20(1).png)



