“To make all athletes better through passion, design, and the relentless pursuit of innovation,” is Under Armour's stated mission. They have certainly delivered on the innovation promise in their products. Today, we will look at their innovation a few layers removed from your moisture-wicking socks or state-of-the-art Olympic speed skating suits.
Under Armour has several digital products, such as MyFitnessPal, under the umbrella of Under Armour Connected Fitness. It is here that Kyle Rockman (@Rocktavious) is an infrastructure engineer. He codes infrastructure that supports the software engineers' applications that you use to track protein shakes and Twinkie consumption. Kyle spoke at the AllDayDevOps conference about how he and his team are innovating. Specifically, their tool to compose and share hierarchical environment variable configuration to make updating hundreds of microservices easy. Yes, it is true. They were able to make it easy to share environment variables and make the updating process more transparent and easy.
How To Share Secrets
During his talk, Escrow: How To Share Secrets, he outlined how they allow anyone to manage configuration data that is shareable and allow for integration with any future systems. This fits within their goal to, “Empower UA engineers to frictionlessly deliver excellent software experiences directly to our consumers.” This overarching goal rests on top of a few key pillars:
- Make the powerful simple
- Make teammates more effective
- Things will break — just don’t let them break the same way twice
- Iteratively create the platform in the open
- Protect the house (PTH) — data is sacred
The problem his team was facing is that they are a small team of support engineers supporting an ever growing organization. In this case specifically, they need to manage configuration data as it relates to the service owner, and the number of service owners continues to grow. They needed to find a way to relieve the pressure.
They decided they needed to:
- Enable self-service
- Protect the data but make it easy to share and use collaboratively
- Have an access control list on configuration data
- Implement API first to allow for future integrations
- Ensure updating the configuration data across multiple services is easy as possible
- Provide for integration with any future platforms
Building Escrow
Their team developed Escrow. The word escrow means, “a bond, deed or other document kept in the custody of a third party, taking effect only when a specific condition has been met.” They thought this described the tool they were building.
Escrow, the tool, is built on a couple primitive concepts. To start, a Link is an individual piece of ‘key=value’ data that can be shared in a Chain, which is an ordered collection of Links. In other words, Links are just variables which can be ordered in an hierarchy, and the Chain provides the hierarchy.
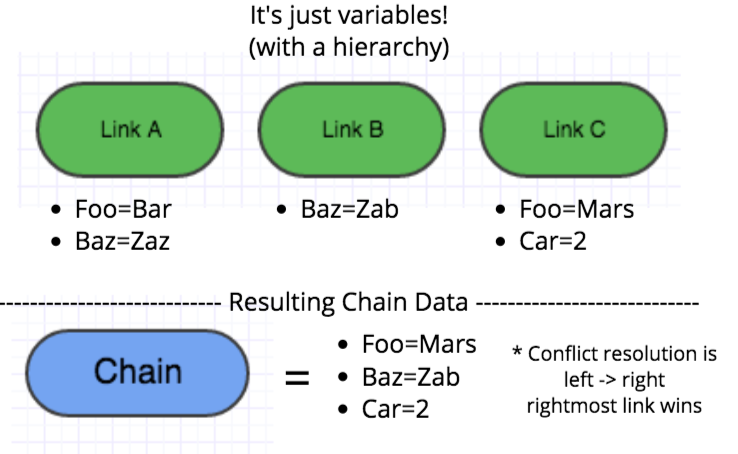
So, Escrow Chains are tools to compose key value data, and they flow into Escrow Artifacts, which are an immutable chunk of data that can be reused anywhere. This is important because when a Link is changed, it is changed in all Chains. To help preserve states when needed, Chains are rendered into Artifacts to ensure changing a Link will not change the value in the Artifact if you don’t want it to change.
Kyle talks about how they handle privacy and APIs, how they bootstrapped it, and he shared some of the UI. He also mentioned their are trying to open source the tool. if Escrow looks like a tool that could be valuable to your organization or that you would want to contribute to, keep an eye out on Under Armour’s GitHub.
In the meantime, Kyle’s talk goes into much more depth on how the tool works. You can watch his full talk here.
photo: Lascot Studio



.png?width=610&name=J1_ModernCybersecurityBook_Promo%201200x628%20v2@2x%20(1).png)



